(Information in italics courtesy of BOERGER CONSULTING, LLC)

image courtesy of connectedgear.com
All businesses today receive benefits from Information Technology (IT) but many still consider it a problematic cost center of their business. As technology has progressed, more forward-thinking organizations have started to see IT as a valuable tool and an investment in their business’s future. Still, every business is looking to reduce costs and IT is often the first place they look to trim their budget.
Some of the traditional ways IT cost has been reduced started in IT hardware with the origin of cloud computing and virtualization. Virtualization is a software system that allows IT hardware to provide much greater capacity and functionality, reducing hardware costs. Other popular cost savings have come from hiring less expensive personnel such as interns or outsourcing IT personnel entirely. A more recent trend has been to utilize open source software for business processes. Open source software is developed within a community and offered for free with options to pay for technical support. However, many businesses and business functions don’t have the flexibility for open source and are required to maintain relationships with the software companies, utilizing expensive and complex licensing for their software. This has led to larger organizations taking cost reduction steps by investigating their physical assets and software licenses — a practice commonly referred to IT Asset Management (ITAM). The savings in both cost and time are staggering with a proper business management plan.
Boerger Consulting, a partner firm of Two Ears One Mouth IT Consulting (TEOM), is an innovator in the ITAM consulting realm. Their focus is helping businesses reduce the overall operational cost of their IT department by properly managing, measuring, and tracking their hardware and software assets. According to Boerger Consulting, the threat is real:
“Some software publishing firms rely on software license audits to generate 40% of their sales revenue. These companies wait and watch your volume license agreements, your merger & acquisition announcements, and the types of support tickets called in, to pinpoint exactly when your organization is out of license compliance. They count on your CMDB and SAM tools to be inaccurate. They make sure the volume license agreement language is confusing and convoluted. And they make sure their auditors always find something – unlicensed software, expired warrantees, unknown network segments – to justify your penalty.”
The payoff, however, is also real. Citing a 2016 paper from Gartner, Boerger Consulting suggests an organization could eliminate THIRTY PERCENT (30%) of their IT software budget with a proper software asset management (SAM) program:
“Part of that savings is finding the hardware and software lost in closets and under desks and odd corners of your warehouse. Another part is identifying and eliminating licenses, support, and warranties for programs and hardware your organization no longer needs. The last part is proactively locating and eliminating audit risks before the auditors do, and then pushing back on them when it is time to renew your volume license agreements.”
Although we focus on different technologies, a synergy has been created between TEOM and Boerger Consulting. We have found that when a business makes the decision to move their IT infrastructure off-site unforeseen challenges can occur. These challenges can be related to privacy and data protection compliance, resulting from retiring on-premises servers, or it may be that there are different software licensing practices required in the cloud. These are two examples of issues that TEOM and Boerger Consulting can solve.
If after reading this article you still have questions about any of these technologies, Jim Conwell and Jeremy Boerger would be happy to meet for a free initial consultation. Please contact:
Jim Conwell (513) 227-4131 jim.conwell@twoearsonemouth.net
we listen first…


 cloud trends for last year[/caption]
cloud trends for last year[/caption]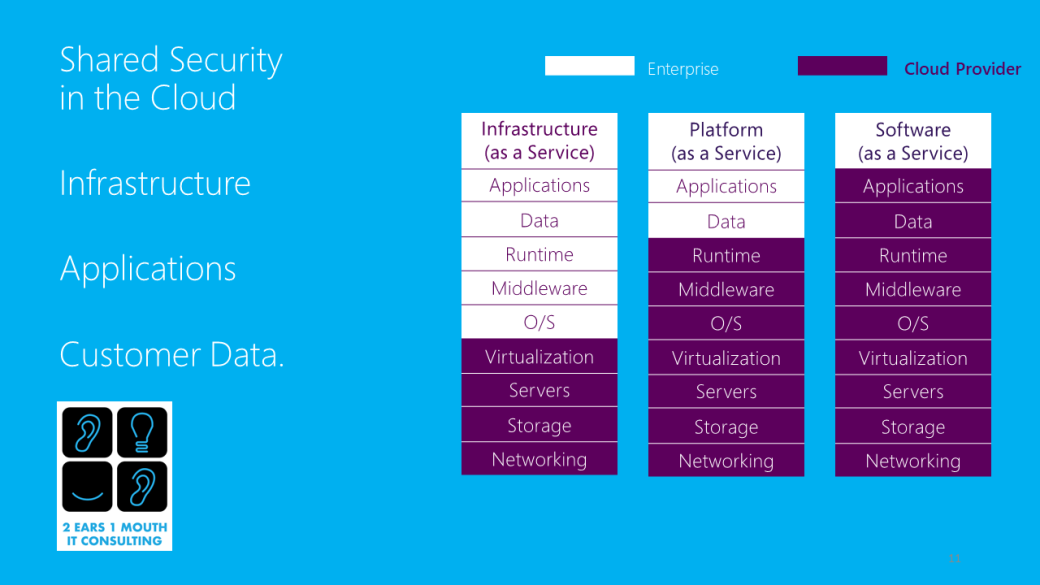 cloud security is shared[/caption]
cloud security is shared[/caption]